Privacy/Surveillance/Ubiquity
This project's aim is to explore some of the ways in which the ubiquity of digital technology has opened up many questions about privacy and the risks and moral questions thrown up in the increasingly complex world of surveillance and intrusion. The contradictions and anomalies are highlighted by poets and artists to see our way through and survive and help us understand our predicament. I include and artefact as a how-to on the use of hacking tools 'Driftnet' and 'Ettercap'.
produced by: James Tregaskis
Privacy/Surveillance/Ubiquity
The state of being apart from other people or concealed from their view; solitude; seclusion/the state of being free from unwanted or undue intrusion or disturbance in one's private life or affairs; freedom to be let alone/freedom from damaging publicity, public scrutiny, secret surveillance, or unauthorized disclosure of one’s personal data or information, as by a government, corporation, or individual/the state of being concealed; secrecy/Usually, privacies. Archaic. a personal matter that is concealed; a secret. /
Archaic. a private or secluded place.
The purpose of this essay is to explore some of the ways in which the ubiquity of digital technology has opened up many questions about privacy and the risks and moral questions thrown up in the increasingly complex world of surveillance and intrusion. The challenges posed by technology and its accelerating pace pose a significant problem for lawmakers and politicians alike. The contradictions and anomalies are highlighted by poets and artists to see our way through and survive and help us understand our predicament. Surveillance and privacy and the lack thereof, accumulate daily as a symptom of our malaise. The challenges of ubiquitous computing and its concomitant privacy concerns are also examined, our privacy concerns should not be solely focused on our reputation/social harm but may well extend to life threatening scenarios e.g. if we become victims of malicious attacks, on a single instance or across a continent. The artefact accompanying this essay, a small DIY project I describe later, shows how quickly and easily one can use tools for breaking through into the privacy of others.
Robert Schifreen and Steve Gold were taken to court in 1988, using a password obtained from a BT engineer, they found a way to hack into Prince Philips’s Prestel account. At the time it was not an offence but it led to the incorporation in 1990 of the Computer Misuse Act. In 1984 I ran a bulletin board (called Mega-Anchovy) running on a 1200/75 modem and a BBC micro. Mega-Anchovy became the subject of a one page article in the Observer supplement that year. A popular section on the Mega-Anchovy bulletin board was to exchange passwords to enter into computer systems. At that time, it was fairly arcane, restricted to a few people who 'did not visit pubs much' and before the 1990 act was introduced. I too hosted passwords to enter Prestel and one or two US based sites. This was ten years before the internet; Fidonet, CBBS and stand-alone systems were popular among computer hobbyists and were set up in the innocent early days before Facebook and Buzzfeed.
As technology progresses it becomes more problematic to develop and evolve moral codes to keep up with change and this in turn has reflected in legal cases e.g. Glen Mulcaire the private investigator and Clive Goodman were jailed in 2007 for hacking over 4700 victims in collusion with the News of the World. This has presented lawmakers a dilemma: freedom of speech balanced against privacy in the context of journalism. Following the News of the World phone hacking, there followed the Leveson enquiry in which was concluded that the existing Press Complaints Commission is not sufficient. The prime minister David Cameron supported the findings but expressed "serious concerns and misgivings" concerning implementing changes to the law.
The search engines I use to research this paper use DuckDuckGo or StartPage, rather than Google as it is known to retain and collect a user’s browsing history [i] - Google’s quote …” a few ways we use data to make our services faster, smarter, and more useful to you…”
Larger internet companies such as Facebook have ‘crossed the line’; breaking European privacy laws (2016) Facebook Ordered to Stop Tracking Non-Users in France[ii], since it modified its privacy policy in 2014[1], also in Belgium, again, tracking non-members of Facebook[2]. There are many more examples of the leaking of private information; post-Snowden and the Panama Papers[3] . At the time of writing, the news story was broken by the whistle blower Christopher Wylie regarding Facebook and Cambridge Analytica.
There is a mismatch between the application of law to and the penalties applied to tech companies and individuals. For example, a company may be fined a small proportion of its overall profits whereas an individual may face prison.
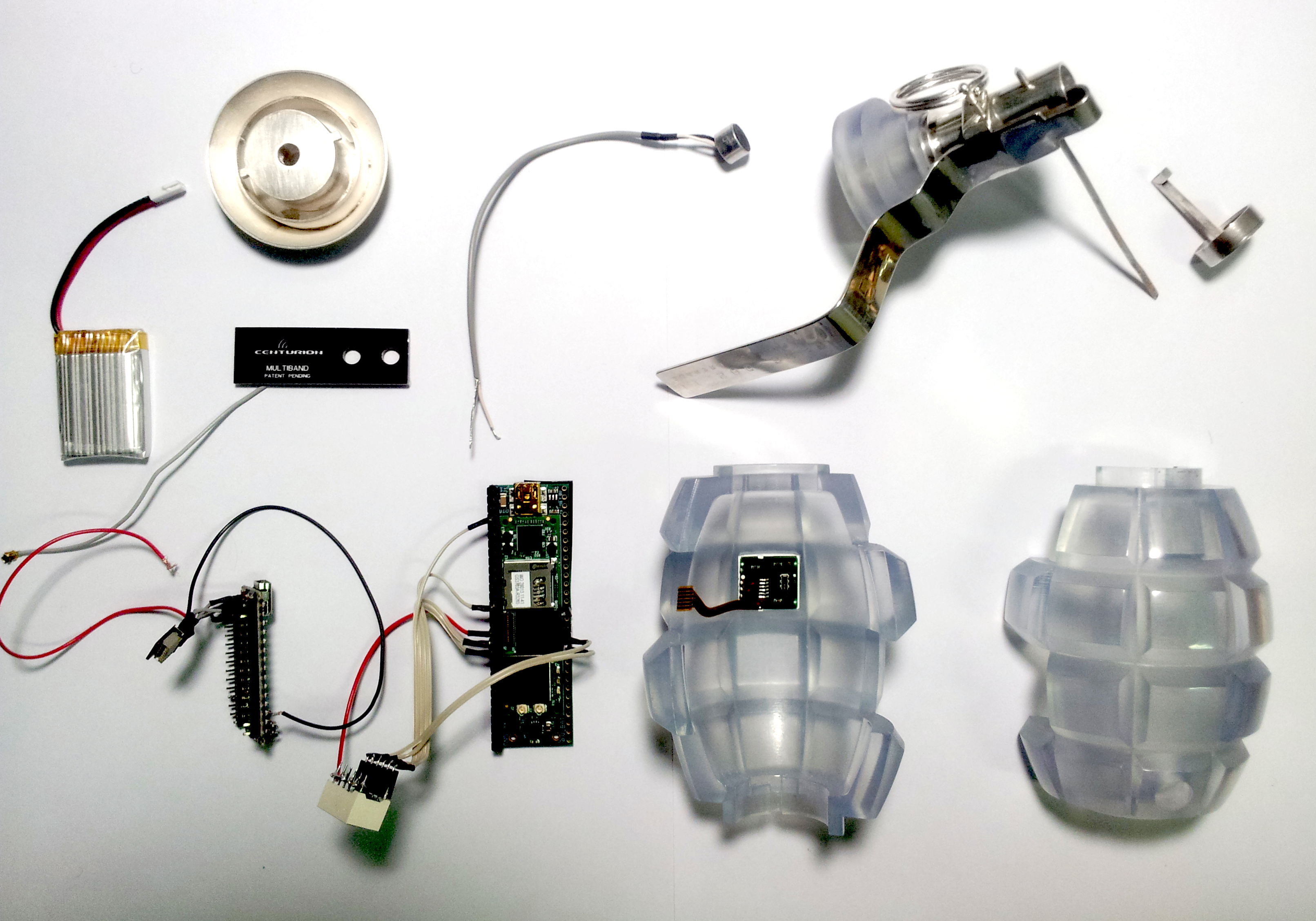
Julian Oliver has explored the questions raised in networking and privacy; in 2017 I came across his work, “Newstweek” (2011), in the “How much of this is fiction” exhibition at the Fact Gallery, Liverpool. In this work, many devices, planted near Wi-Fi hotspots ‘, fed out manipulated news stories’ to unsuspecting audiences on the internet. Oliver has provided us with many examples of the mysterious interplay between our physical world and the virtual networked domain.
(See Gallery) Figure 1: The Transparency Grenade [disassembled], a handheld network intervention device. Julian Oliver 2012
The internet moves quickly, people are exposed to privacy and transmission of misdeeds with incredible velocity. Back in 2005, a girl in the Korean subway fails to pick up her dog’s business and is photographed and rapidly circulated, the meme quickly becoming known as ‘the dog shit girl’ . Rumour and even lies become quickly propagated across the web. However, the dog poop girl case galvanised peoples reaction to force a norm; to clean up after one’s dog. Norms, are social attitude of approval and disapproval. An interesting example of ontological emergence!
Privacy is seen by many as precious commodity; Hasan Elahi has turned this inside-out. He has documented, photographed and publishing every detail of his life online. He has sent huge amounts of information about himself; self-reporting his activities to the NSA. This includes visits to the lavatory, his slept in bed, views outside his window, his front room etc.
Elahi states that he has been put on the NSA terrorist watch list, possibly as a result of his sending sousveillance/surveillance art[4]. Web Cam Surveillance Elahi website
The government tracking and surveillance of its own citizens is nothing new, but since the introduction of the Patriot Act in US after 9/11 and the advances in technology, the NSA continued to monitor, without obtaining a warrant, phone calls, internet activity, text messages and other communication, even after it was revealed and requested that it should cease[5]. Subsequently, Edward Snowden revealed in 2013, the existence of PRISM [6](NSA) and the Tempora [7]programme (GCHQ).
The exhibition at Tate Modern in 2010 entitled “Exposed Voyeurism, Surveillance and the Camera” included works by Guy Bourdin, Henri Cartier-Bresson, Philip Lorca diCorcia, Walker Evans, Robert Frank, Nan Goldin, Lee Miller, Helmut Newton, Man Ray. This show included 250 works by various artists; mostly using (covert) photography as the medium, the technology available at their time. By intruding into peoples’ privacy, the artists have captured the materiality of intimate moments. Warhol used the cine camera in a similar way, and later on, video to film his subjects to the point that they were barely aware they were being filmed. Post Warhol, the advent of computer networks had just begun and we now we are able to witness its transformative effects. In its emergence it was seen as a tool which would grant agency to individuals to affect political discourse and create change, for example, the Arab Spring. We are still only barely aware that its intrusion into our privacy means that when our personal details fall into the wrong hands the ability to psychologically profile us means. we can be manipulated and controlled in ways we are unaware of viz. Cambridge Analytica, fake news stories etc.
No-one could have predicted this state of affairs back in the times of Leo[8], the accounting computer company developed by Lyons corner house[9]. Perhaps this is an another example of ontological emergence of technology.
Perhaps the most intriguing artist I came across is Steve Mann, the originator of the term Sousveillance and dubbed the father of wearable computing[10]. Living as a cyborg for thirty years, he constructed a wearable art gallery in which anyone can exhibit work.
To quote Mann from the abstract of the book “Sousveillance and Cyborglogs: A 30-Year Empirical Voyage through Ethical, Legal, and Policy Issues”:
“The most interesting of these accidentally-found questions pertain to: (1) inverse surveillance (body-borne audio-visual and other sensor capture, storage, recall, and processing, known in the research literature as “Sousveillance”); and (2) the epistemology of freewill and metaphysics of choice that seems to arise from an apparent reversal of the now pervasive and ubiquitous notion of surveillance.” (Mann)
(See Gallery) Figure 2: Evolution of Sousveillance Mann 1999 - Memoto 2013
Memoto updated concept first proposed by Steve Mann; the device takes periodic photos so that this can be used and displayed at a later date, anyone can buy Memoto and practice Sousveillance – yet another gadget or as a tool for counter-surveillance.
I videoed this short clip of a scuffle with police in 2011 in Panton Street during one of the many demonstrations during that year. The police habitually filmed the demonstrators, and the demonstrators filmed them back.
Another manifestation of invasion of privacy is wireless identity theft, gathering a person’s identity from RF-enabled id cards, e-Passports [11]and bank cards. Each of this type of card carries with it an RFID chip, responding to certain frequencies. Scanning these cards, either via a reader being used before the postman delivers it or by ‘drive by attacks’ renders an individual vulnerable to identity, financial theft or being cloned. It is worth noting the irony of providing advice on data security in the context of wireless identity theft; Experian, the world’s biggest consumer credit monitoring firm who were hacked and leaked the identity of thousands of customers offering advice on protecting oneself! I was one of the victims and a and an apology was posted to me six months later after they had knowledge of the attack.
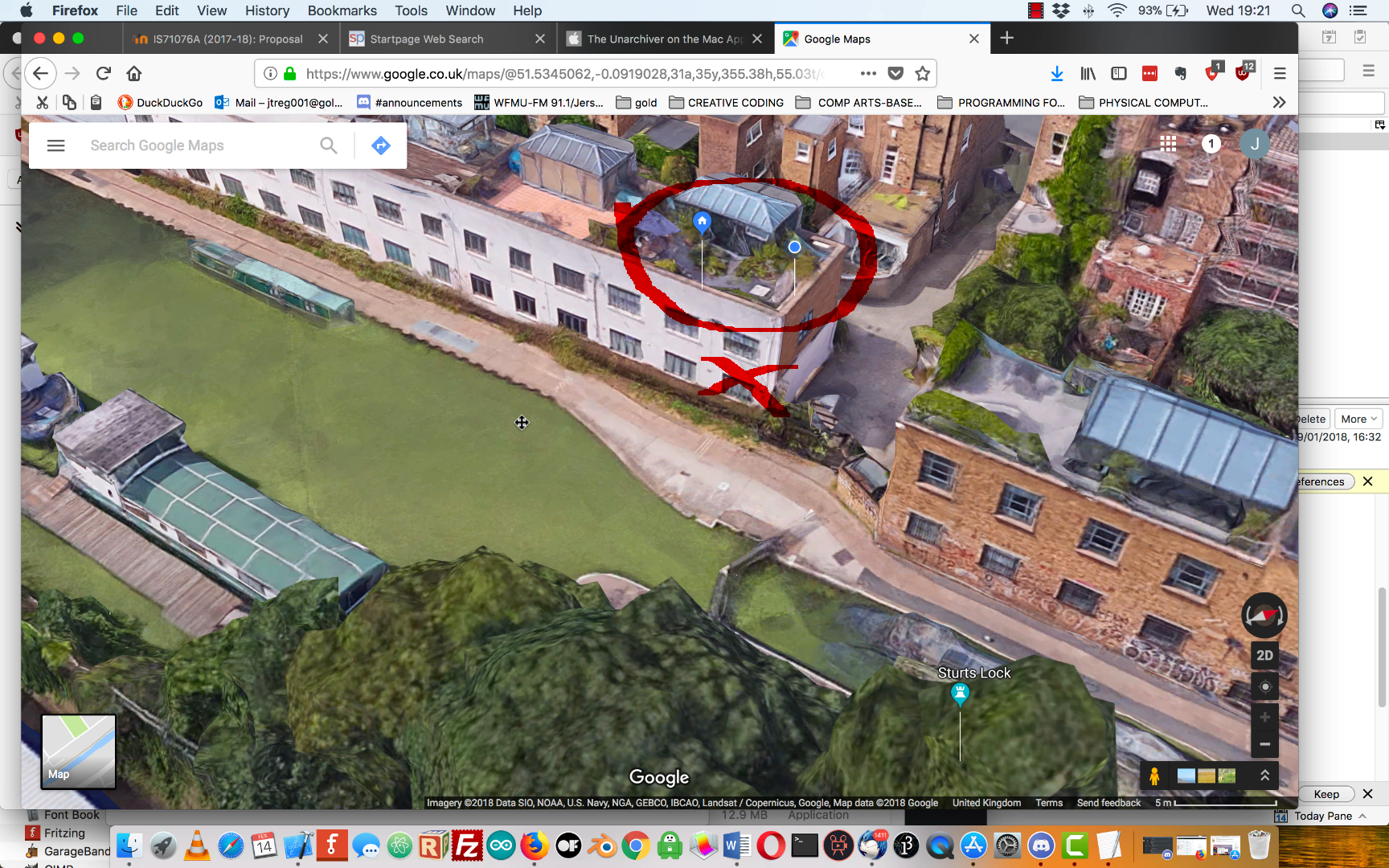
(See Gallery) Google – closer than you think! Previous incarnations of Google Map Satellite used to show houses as little blobs. (This image taken over a year ago)
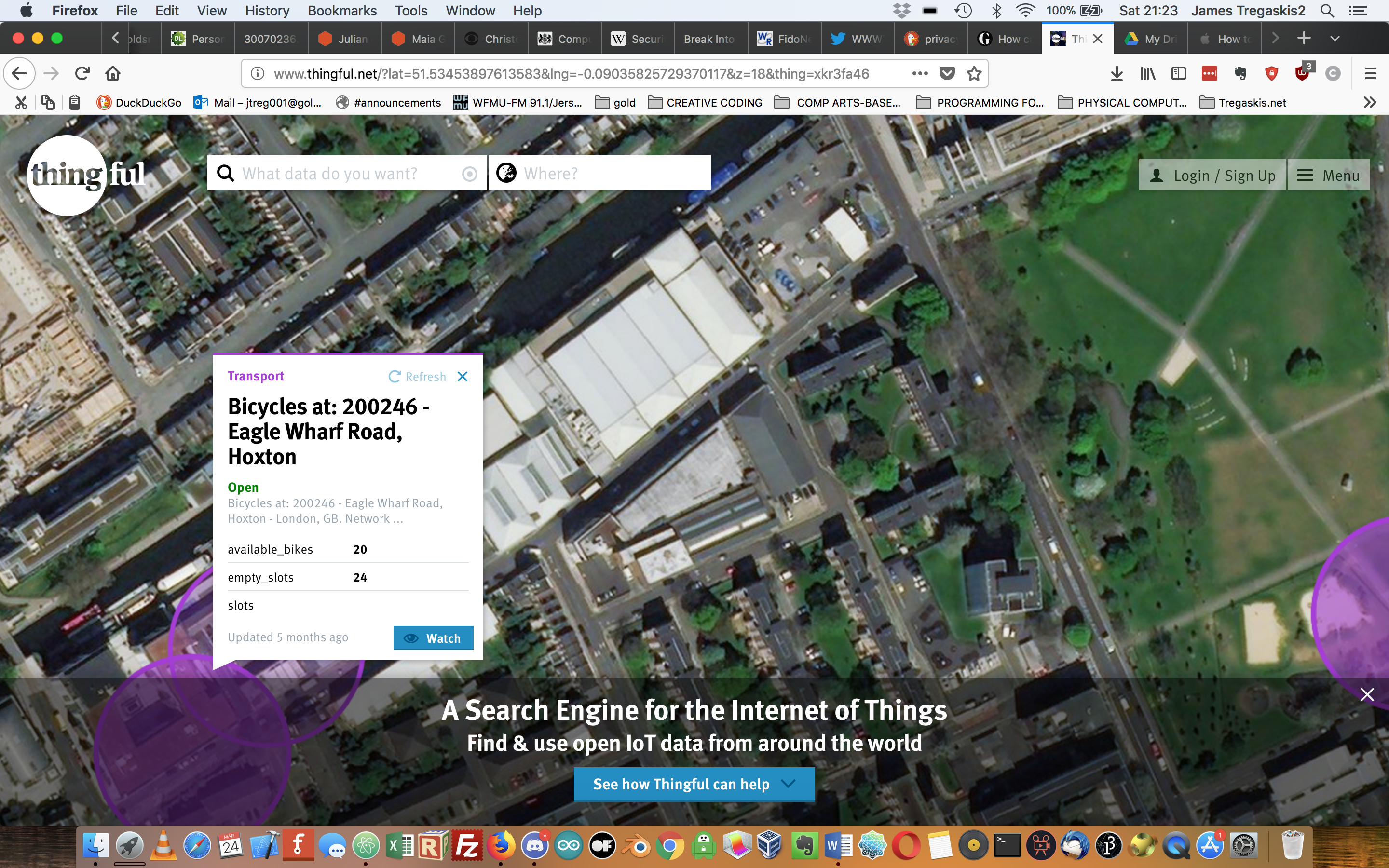
(See Gallery) Available bicycles over the canal. Now.
IoT (Internet of Things pose new challenges to preserve our data security (i.e. privacy) – Usman Haque anticipates great demand for his IoT ‘search engine’ concept; www.thingful.net. Rob van Kranenberg sees IoT data as a commodity that users can auction and sell. Perhaps this is possible but what if data breaches occur?
Google Glass launched in 2014 and discontinued in 2015; a big failure. Was this marketing failure or resistance by the public to overt privacy intrusion?
(See Gallery) Figure 3: I would never buy one of these!
Data about our personal lives to a granularity that is even finer, perhaps the new ‘Non-Human Turn[12]’ as coined by Richard Grusin? This may be an even greater challenge to our privacy – unauthorised sharing of personal data – perhaps this could have already taken place in the IoT space.
Threats to commerce, the potential for spying and disruption can take place on an ever-increasing scale. The commercial pressures to bring IoT devices to market may result in a lower priority to implement security measures, e.g. leaving the default settings in Linux on the device not using https, no mechanism for security updates, etc. Thus, this renders our homes and businesses open to criminal intrusion. Governments are just waking up to this vulnerability and we would expect to see more proactive measures being put into practice[13].
Charlie Miller and Chris Valasek in 2015 demonstrated how a car’s internal computer systems can be compromised [14] externally - making it possible to endanger the passengers. This culminated (in the US) “the number of vehicles that were vulnerable were in the hundreds of thousands and it forced a 1.4 million vehicle recall by FCA as well as changes to the Sprint carrier network”
(See Gallery) Figure 4: Nuage VerteHelen Evans and Heiko Hansen and their project "Nuage Vert" or 'Green Cloud' is using a city-scale light installation to alter perceptions on pollution and increase participation among the cities local population.
As well as HeHe (Fig.4) Steve Mann, Julian Oliver and Hasan Elahi are three examples of artists who hold a lamp up to highlight problems in privacy/ubiquity/public safety. They have pioneered and inspired other artists to consider the ubiquity of IoT and our connected world, this site also holds a few more examples. The companies providing IoT devices have the responsibility to ensure the device/service is secure from data theft and/or being compromised.
For my artefact into privacy I investigated how to monitor Wi-Fi networks and obtain information, to teach myself how to obtain and install and use Wi-Fi hacking software using network penetration tools Ettercap and Driftnet running on Kali Linux. I had planned to take the Raspberry Pi into a public Wi-Fi area and record images. However, mindful that using these tools to sniff Wi-Fi traffic is a criminal offence under the Computer Misuse Act. I learned how to set it up at home and harvest images there. For the purposes of publication, I can only offer illustrations of the types of information I might have obtained, had I followed my original plan. Most of them might have originated from my wife who might have browsed on her computer upstairs, images such as houses on property websites, clothes and shoes. Other images might have been either from neighbours looking at http://www.express.co.uk/ or http://www.dailymail.co.uk/home/index.html - both of which have unencrypted pages. One extension of the use of Kali Linux might be to use Wireshark to capture data streams in Wi-Fi (or across wired networks) in order to log passwords and email texts but I decided that was too unethical. I question why the law prohibits me from examining open Wi-Fi traffic, I could just as easily listen into other people’s conversations on the bus. Also, how easy would it be to police this proactively? I have investigated how easy to set up tools for ‘spying’ as it is to buy a kitchen knife in a shop. Artists such as Julian Oliver have skilfully used these networking techniques and used them to reveal startling stories – mining a rich vein of emergence.
*(http:// not https://).
References
The Offensive Internet Edited Saul Levmore, Martha C Nussbaum
The Future of Reputation; gossip, rumour and privacy on the internet Daniel J Solove
https://www.kali.org/
Richards, Neil M., Watching the Watchers (November 4, 2013). Wired Magazine, The Wired World in 2014 (UK Edition), 2013. Available at SSRN: https://ssrn.com/abstract=2350002
http://hehe.org2.free.fr/?cat=12&language=en (Nuage Verte)
Blank Spots on the Map: The Dark Geography of the Pentagon's Secret World, Trevor Paglen
Instructions for Artefact:
Install Kali first – I used a Raspberry Pi Model 3 B
Download the Kali Image from Offensive Security website
Burn the image onto 16 Gb Class 10 SD card (I used Etcher).
Login as root pw toor
Open a terminal window, type:
apt-get update
apt-get upgrade
install the tools we need by typing:
apt-get install kali-linux-wireless
Reboot the Pi.
open a terminal window and type
ettercap -T -Q -M arp -i wlan0
(you can use the gui but this will get you started via the command line)
Open another terminal window
And type:
urlsnarf -i wlan0
Open another terminal window, type:
driftnet -i wlan0
You might see some images appear!
Note:
I include the types of images you might see as examples of unencrypted http streams will be attached separately to this essay. (See Gallery)
James Tregaskis 28th March 2018
References:
[1] Facebook Debuts ‘Privacy Basics’ And Updates Policies To Reflect More Personalized Ads https://newsroom.fb.com/news/2014/11/updating-our-terms-and-policies-helping-you-understand-how-facebook-works-and-how-to-control-your-information/
[2] https://techcrunch.com/2015/11/11/facebook-faces-privacy-fines/
[3] https://www.nytimes.com/2016/04/05/world/panama-papers-explainer.html
[4] https://www.thedailybeast.com/the-orwell-project-hasan-elahis-anti-terrorism-art
[5] Savage, Charlie; Risen, James (March 31, 2010). "Federal Judge Finds N.S.A. Wiretaps Were Illegal". The New York Times.
[6] https://www.theguardian.com/world/2013/jun/06/us-tech-giants-nsa-data
[7] https://www.wired.co.uk/article/gchq-tempora-101
[8] https://www.telegraph.co.uk/technology/news/8879727/How-a-chain-of-tea-shops-kickstarted-the-computer-age.html
[9] https://flashbak.com/the-rise-and-fall-of-the-lyons-cornerhouses-and-their-nippy-waitresses-35186/
[10] Personal and Ubiquitous Computing Volume 7 Issue 5, October 2003 An EyeTap video-based featureless projective motion estimation assisted by gyroscopic tracking for wearable computer mediated reality Chris Aimone, James Fung, Steve Mann
[11] Heydt-Benjamin, Thomas S; Bailey, Daniel V; Fu, Keven E; Juels, Ari; O’Hare, Tom (October 22, 2006), Vulnerabilities in First-Generation RFID-enabled Credit Cards (PDF) (draft study), Amherst, MA; Bedford, MA; Salem, MA: University of Massachusetts; RSA Laboratories; Innealta, retrieved 2009-03-14.
[12] Grusin, Richard. "Introduction". In The nonhuman turn. University of Minnesota Press, 2015.
[13] https://cybersecforum.eu/files/2018/01/cybersec_2017_recommendations.pdf
[14] http://illmatics.com/Remote%20Car%20Hacking.pdf
[i] https://privacy.google.com/your-data.html
[ii] https://techcrunch.com/2016/02/09/facebook-ordered-to-stop-tracking-non-users-in-france/